The World Economic Forum lists data breaches and cyber-attacks alongside natural disasters and climate change as the top global risks in 2021.
Email still happens to be one of the most common vectors by which enterprises are attacked. The importance of implementing email security best practices therefore cannot be overstated, especially as most enterprises rely heavily on this channel for everyday business communications. Cybercriminals can easily exploit the overlooked vulnerabilities of corporate email security through distributed denial-of-service (DDoS) and phishing attacks, malware and ransomware, and employees’ mistakes.
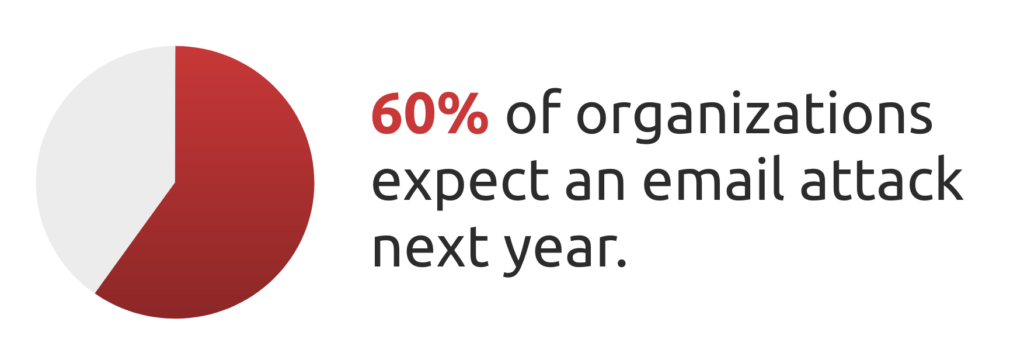
According to the Mimecast State of Email Security 2021 Report, sixty percent of organizations stated that an email attack is inevitable or likely in the coming year.
Poor email security can cause data loss and downtime as well as leaks of confidential information about a company’s financials, intellectual property, employee and customer information. Losing control of such sensitive documents can also lead to loss in revenue and market share, fines and reputation damage. This is especially true for those in highly regulated industries such as finance, legal, publishing, education, and healthcare.
Yet enterprises have still not developed a cyber resilience strategy that emphasizes email security. Specialized standalone email security solutions are available to combat each type of attack. But IT departments need comprehensive visibility and control over the enterprise’s overall email security strategy and defense. This is the only way they can make sure they’re protected against every possible type of attack.
Here are four email security best practices to incorporate in your enterprise’s overall cyber security strategy.
Best practice #1 – Improve your endpoint and email security hygiene
Endpoint email security encompasses a variety of tools and processes that protect end-users’ devices from being compromised through email-delivered attacks. Employees can be targeted with phishing emails, spam and malware which if opened could infect their devices and provide gateways for hackers to access the entire enterprise network.
To combat this, enterprises should install endpoint email security software in combination with anti-virus protection tools. These can filter and block malware or spam emails from suspicious senders and IP addresses and clean up infected systems from sending outbound spam.
Specifically, endpoint security software can confirm whether a device meets security policies before allowing it to access an organization’s network. Remote devices that haven’t updated their operating systems, have their firewall turned off, or have other specifically recognized security flaws are denied access so that outside threats to the network are mitigated.
Email is also used by malicious actors to execute zero-day attacks that exploit previously unknown defects in software, hardware, or firmware. A basic countermeasure against this would require your IT team to upgrade and patch all endpoints on a regular basis. While this does not stop zero-day attacks entirely, it will reduce their chances of success or at least buy you more time until the relevant zero-day patch becomes available.
Another key component of endpoint protection involves implementing enterprise-wide policies on basic password and corporate email security best practices. For example, you can instruct employees to:
- Avoid storing passwords on paper notes and in public locations
- Avoid duplicating old passwords or those created on other sites
- Create strong passwords with characters (@) instead of alphanumeric letters (a)
- Use passwords that can’t be guessed by strangers (avoiding names, ages, birthdates, company, social media interests, etc.)
Two-factor authentication should also be mandated, or at least encouraged, for all employees whether through a mobile phone, an app on a device, or authentication tokens.
It also helps to continuously train and test employees on email security best practices, including how to spot phishing emails, so they’re well prepared to avoid and report them. Some enterprises even deploy simulated phishing attacks to test their employees’ readiness.
Best practice #2 – Safeguard your email content with encryption
Fully protecting your email content requires that both the content and attachments are encrypted while in transit and at rest in the inbox. Popular email platforms like Gmail and Outlook typically don’t have the requisite enough enterprise-level email encryption to fully secure organizations against all cyber threats. And to the extent that these platforms do support encryption, they only work if both the sender and recipients have certain extensions enabled.
Third-party add-in encryption services can close these corporate email security gaps. But be aware that some of these encryption services can add significant friction to the user experience. Any encryption tool is only effective if users can easily make it a part of their regular workflow. So, carefully weigh your options by testing out their trial versions before making your final selection. With Digify’s Gmail and Outlook plug-ins, end-users can send encrypted emails and files directly in Gmail or Outlook without interrupting their workflow.
Document security solutions are also effective in preventing unauthorized access to your confidential information shared via email. These solutions work by giving you control over who gets to view, print, and download your documents. You can even revoke access to the recipient after sending your emails. Meanwhile, expiry settings, watermarks, screen capture protection, and tracking give you more control over keeping your sensitive documents in the right hands without leaking outside. These important document security capabilities should be a part of any third-party encryption service you choose.
Best practice #3 – Implement email server protection
It’s not just the email services that can be hacked but the servers used to store and send the email can also be compromised. Spam and DDoS attacks on these servers can disrupt regular email transfer and processing. They can also be used by hackers as a way to send spam email from your server, harming your reputation and getting you blacklisted.
This is why it is important to protect your email servers. Direct your IT team to enforce sound email server protection techniques, starting with:
- Restricting the mail relay parameter by specifying a list of domains and IP addresses to which your mails can be safely forwarded
- Limiting the number of connections to reduce the chance of spam and DDoS attacks
- Verifying the sender through reverse DNS lookup before accepting incoming messages
- Use content filtering to fight spammers from accessing your server
It is important to work with your IT team to give them all the necessary information to help them secure your email servers. Separating real authentic emails from spam, phishing attacks and other threats early on can be instrumental in keeping your intellectual property and confidential company information secure.
Best practice #4 – Prevent data leakage and breaches
Confidential documents often share certain attributes. They may have similar keywords, data types or rules that can be used intelligently to spot these documents. Your enterprise can prevent the leakage of such sensitive data in emails by filtering, blocking, or censoring based on keywords, expressions, and rules. For example, your IT team can block all outgoing emails with personal information like social security numbers, credit card information, and files with the keyword “confidential” or “internal use only”. A good rule of thumb is to use encryption to protect outbound data while filtering inbound emails to block malware, viruses, and phishing threats.
Data loss prevention (DLP) tools can be applied to prohibit sensitive information from spreading outside your enterprise by alerting your IT admin about violations of data access policies. This allows your IT team to proactively respond to issues instead of trying to repair the damage after a data leak has already occurred. Predictive technologies such as machine learning (ML) and artificial intelligence (AI) are increasingly being used for real-time monitoring to detect unusual data patterns that can identify and impede data breaches.
Without effective DLP tools, your enterprise is risking the unintended exposure of customer data that can result in identity theft, monetary fraud, and the loss of your business reputation. When customers and employees trust your organization enough to share their private data, you have a responsibility to protect it.
Conclusion
With email being at the center of business communications for most enterprises, it is of paramount importance that this channel be secured. Implementing sound corporate email security best practices can help stave off attacks and data breaches. This is key to building trust in your organization’s operations, employees and with your customers.
Adding a third-party integrated email security solution like Digify with compliant document security can ensure that the information you share via email is protected against unauthorized access, download, and misuse. Digify not only encrypts your email content and attachments but also allows you to control access to your files even after sending them. You can view when your attachments are opened by recipients, how long they’re viewed, and if your document is downloaded or printed. Plus, you can configure encrypted messages and attachments to automatically expire after a certain amount of time. Digify uses the AES-256 algorithm to encrypt emails and files, which is certified for top-secret documents.
Your enterprise doesn’t have to sacrifice seamless collaboration to securely communicate confidential business information. See if Digify’s Gmail and Outlook plugins meet your enterprise’s needs by taking advantage of a free trial today.