How important is PDF and document security to your company?
There are many examples where you should ensure that your important documents are protected. At the same time, you need to be able to share those documents with people who need to review them.
The consequences of security breaches can be disastrous for companies. Sensitive information can help competitors to gain an edge, or leaks of confidential data can do serious reputational damage, or fines in the case of compliance frameworks such as HIPAA and GDPR. Companies need to consider the potential legal ramifications of data leaks, including misuse of their intellectual property.
What is Document Security?
Document security covers a few different measures that are designed to protect access and discourage improper use of your PDF or other types of documents.
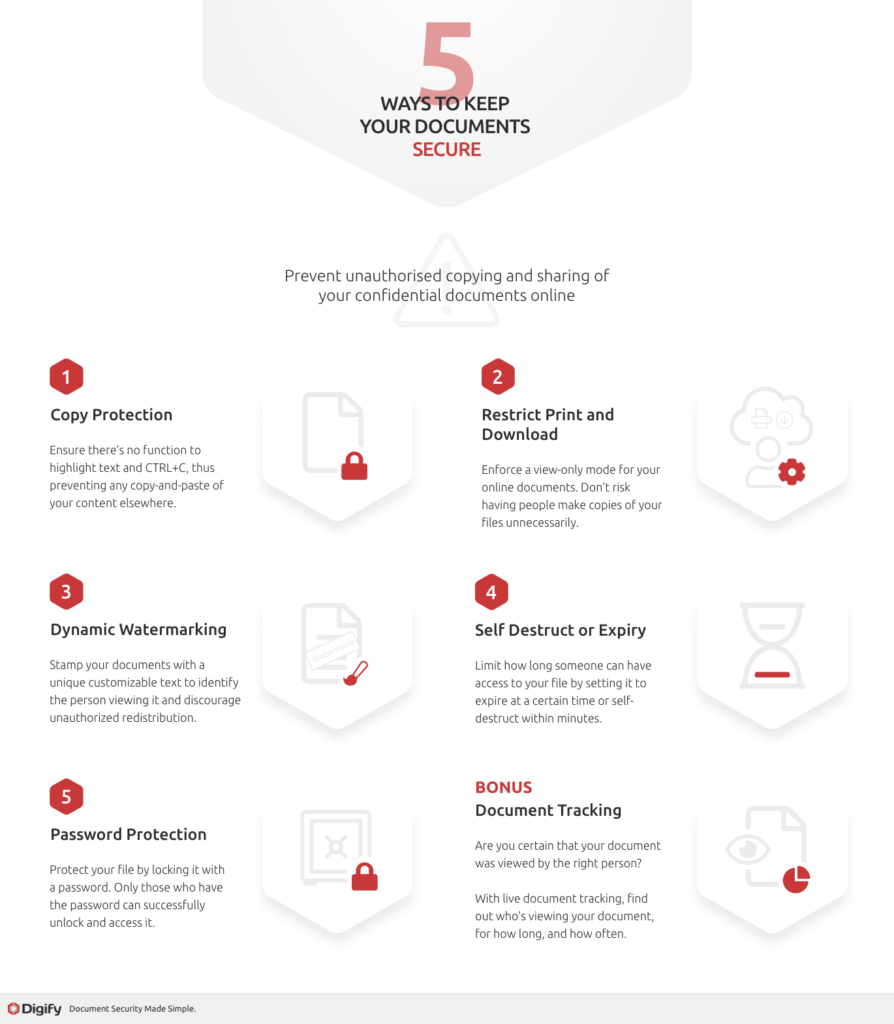
Security measures which are typically used are:
- Password protection
- Watermarking
- Document expiry, self-destruct and restriction of access
- Digital Rights Management: Restricting copy, print or forwarding
- Document tracking of who has viewed
PDF password protection
Password protection is one of the simplest measures anyone can take to protect a PDF or other type of file. While a password is by no means a perfect security system, it puts an extra step in the way for anyone who may improperly try to access a document.
Sometimes people come across files by accident, or at other times, someone may deliberately try to access documents they should not be seeing. Consider situations such as shared folders or shared computers in an office setting, and you can see how files might go further than otherwise intended.
Communication of the file password can be a somewhat cumbersome step. Usually, you would send the file itself by one means, then send the password via a separate channel. Of course, depending on the channels you use for communication, it’s possible the password may get spread further than intended, and there’s nothing stopping someone from sharing it with another person.
Nevertheless, protecting your PDF with a password is one of the easiest steps you can take as a deterrent to improper document access, and it can be especially effective in combination with other security measures.
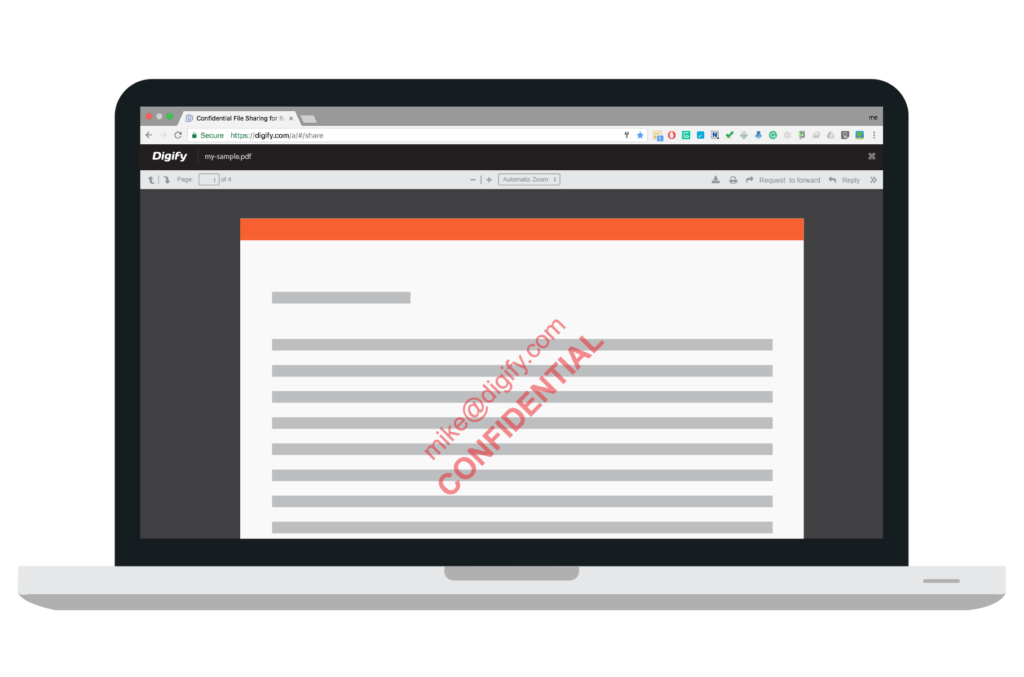
Watermarking
One of the original document security measures, found as early as the 13th Century, is the watermarking of documents. Watermarking has traditionally been used to claim ownership or act as a trademarking device for documents, but in the digital sense, watermarking has further applications.
For example, you might want to discourage the leakage of confidential documents and include some means of traceability should those documents get spread further than intended. One strategy is to watermark digital documents with the recipient’s own email address, thus providing the source of the leak.
A second, more basic application is to communicate the document classification so that recipients know how the document is to be treated. Someone might be much more careful with how they treat a document watermarked “confidential” than they otherwise would with no watermark in place.
Thirdly, watermarking can still be used in the traditional sense, to claim ownership of a document.
Document expiry and self-destruct
There are many possible applications for when you might like to either revoke access to a document, or limit access so that it’s not permanently available to the recipients of a document. For example, consider these potential scenarios:
- An employee has left the company, or a relationship with a contractor has gone sour. You want to ensure that they’re no longer able to access potentially sensitive documents.
- You have a project during which access to sensitive information is required, but you don’t want that information to be accessed on an ongoing basis.
- You have a contract or bid in process for which the offer is only good for a set period of time. You don’t want the offer to be accessible once the deadline has gone by.
- You’d like to prevent a link from being reused after download of a document.
All of these situations can be managed using document expiry, revocation of access and self-destruct features. In fact, many companies prefer to use these access restrictions as a normal part of their document management practices, because otherwise, once a document is sent out, control of it is often completely lost.
Once again, these types of features are often significantly improve document security when used in conjunction with one or more other security features.
Digital Rights Management (DRM)
Digital Rights Management (DRM) enables the control of what the reader can do with the document. DRM is usually in place for documents which contain sensitive information or intellectual property that the document owner doesn’t want copied or spread around.
For example, if you have written a course or ebook, you will want to protect your intellectual property to ensure someone doesn’t copy it and profit from it themselves. If you have confidential documents that you need to send for due diligence, you will want to ensure that those documents don’t go any further than the intended recipients.
Like password protection, DRM is an effective barrier to put in place that impedes your documents from being spread easily. You can prevent printing so that hard copies are not accidentally left where others can find them, as has happened frequently for companies. You can also stop someone from copying the document and pasting it into an email or new document. This means that if anyone wanted to steal your intellectual property, they have a more difficult task ahead of them.
Document tracking
How many times have you sent out a document and been able to say for certain who has seen it, how often it has been opened and from where? What happens quite often is that once a document has been sent, control is lost to the owner – anyone could be viewing your data and you wouldn’t know about it.
This is where document tracking comes in as an important security feature. PDF file and document tracking solutions help you to understand the movement of your documents and whether they are spread beyond your intended audience. You can look at information such as where your document is being opened from and take note if there seems to be suspicious activity. Potentially, if you have other measures in place such as revocation of access, you’ll be able to do something about it.
Document tracking should be considered for situations such as:
- Security concerns. You might be transferring information that is sensitive in nature and you need to be extra careful about how far that document goes.
- Sales and marketing. You can gauge the popularity of a document if you track opens. In situations such as sending a pitch to someone, you can check that they’ve seen it then figure out an appropriate time to follow up.
View this infographic below on the five best ways to keep your document secure.